Building a digital house on sand is a risk no business should take. As organisations migrate to the cloud, the “build it as you go” approach often leads to fragmented security, runaway costs, and compliance headaches stressing engineers’ teams.
At Mobilise Cloud, we believe that the secret to a successful, long-term cloud strategy isn’t just about moving workloads—it’s about where they land, and making sure they land right.
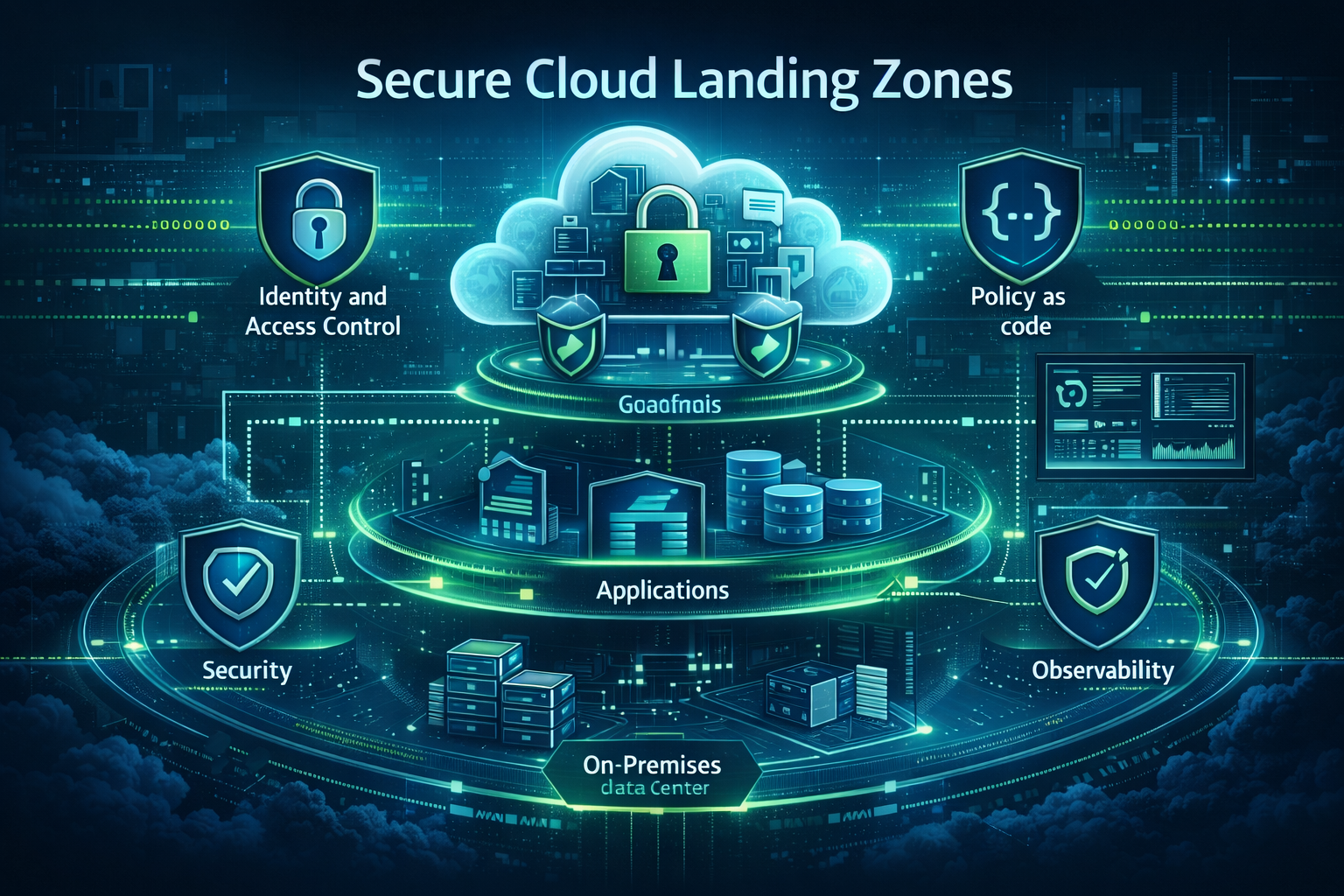
What is a Secure Landing Zone?
Think of a Secure Landing Zone as a pre-configured, “blueprinted” environment where your cloud resources live. It is the foundational layer that ensures every new project, application, or department you launch starts with the same high standards of security, networking, and governance already in place.
Instead of manually setting up security for every new account, a landing zone automates this process. It creates a multi-account environment that is secure by design, allowing your developers to move fast without “breaking” your corporate security posture.
Why it Matters: The Four Pillars of Success
If you are scaling your cloud presence, a landing zone is no longer optional. Here is why:
- Security by Default: It enforces guardrails that prevent common mistakes, such as making a database public or using unencrypted storage.
- Speed to Market: Developers can “vend” a new, fully compliant account in minutes, rather than waiting weeks for IT to manually approve and configure the infrastructure.
- Cost Control: Centralised billing and resource tagging mean you always know exactly who is spending what, helping you avoid “cloud bill shock.”
- Audit Readiness: With centralised logging and auditing, you have a single source of truth for compliance, making your next audit a breeze rather than a burden.
The Engine Room: A Closer Look at Landing Zone Core Components
To understand why a secure landing zone is so effective, we need to look at the “machinery” running under the bonnet. Here are the four functional areas that provide your teams with the help they need:
1. The “Vending Machine” for Accounts
In a traditional IT setup, requesting a new environment takes weeks. In a modern landing zone, we implement Account/Subscription Vending. This is an automated process where a developer clicks a button, and the system “vends” a brand-new account that is already connected to your network, tagged for billing, and pre-loaded with security guardrails.
2. Hub-and-Spoke Networking
We typically architect networks using a Hub-and-Spoke model.
The Hub: Acts as the central gateway. It houses your firewalls, shared services (like DNS), and hybrid connections back to your on-premises data centres. Giving you centralised control of your network.
The Spokes: These are isolated pockets for your workloads (Production, Development, HR, Finance). Traffic between spokes must pass through the hub, allowing you to inspect every packet and block threats instantly.
3. Policy-as-Code (The Digital Security Guard)
Instead of a manual “checklist,” security is written into the cloud’s code. If a user tries to create an unencrypted database, the Policy-as-Code engine automatically blocks the action. This ensures compliance is “always-on” and self-healing.
4. Centralised Observability
A secure landing zone funnels every log, alert, and metric from across your entire cloud estate into a single “Security Operations” account. This gives your security team a “God’s eye view,” making it impossible for a rogue resource or unwanted actions to go unnoticed.
Key Architectural Considerations
When we design your landing zone, we don’t just use default settings. We weigh several critical architectural factors to ensure the environment grows with you:
Organizational Hierarchy
The way you group your cloud accounts matters. We design hierarchies based on Business Units or Life Cycle stages (e.g., Prod, Test, Dev). This prevents a mistake in a “Sandbox” environment from ever impacting your “Production” customers.
The Identity Perimeter
In 2026, identity is the new firewall. We consider how to federate your existing corporate logins (like Microsoft Entra ID) into the cloud. We enforce Just-In-Time (JIT) Access, meaning admins only get “keys to the kingdom” for a limited window when they need to perform a task.
Data Sovereignty & Residency
For UK-based businesses, ensuring data stays within UK regions is often a legal requirement. Our architecture includes “Regional Deny” policies that physically prevent data from being stored in jurisdictions that don’t meet your compliance standards. Want the data to stay in the UK? It stays in the UK!
Scalability and IP Planning
One of the most common pitfalls is “running out of space.” We meticulously plan your IP Address Management (IPAM) so that your network can scale from 10 applications to 1,000 without requiring a massive, expensive network redesign later.
Why Partner with Mobilise Cloud?
Setting up a landing zone is simple in theory, but the complexity lies in the bespoke configuration required for your specific business needs. A “one-size-fits-all” template rarely meets the rigorous demands of regulated industries or complex enterprise environments.
At Mobilise Cloud, we don’t just “turn on” these services. We work as your partner to:
- Architect a structure that mirrors your organisational needs.
- Implement advanced security guardrails aligned with NCSC or ISO27001 standards.
- Automate the deployment using Infrastructure as Code (IaC), ensuring your landing zone is repeatable and future-proof.
- Train your teams so they can take full advantage of the new, high-speed environment.
So you can be safe in the knowledge from day one of your teams working in the cloud will be safe, secure and ready to go at speed and scale.